|
Frequently Asked Questions about
the ISO/IEC 27000 standards
This section of the ISO27k FAQ addresses the following general/basic questions relating to the ISO/IEC standards:
FAQ: “The titles of some ISO27k standards mention ‘Information Technology -- Security Techniques’. Does this mean they are IT-specific?”
A: No, certainly not! The formal titles simply reflect the original name of the joint ISO + IEC committee that oversees their production, namely SC 27 “Information Technology -- Security Techniques”, itself a subcommittee of JTC 1 “Information Technology”.
ISO/IEC JTC 1/SC 27 adopted a new name in 2019 becoming “Information security, cybersecurity and privacy protection”. The new name is gradually being applied to the standards as they are revised and published.
The scope of the ISO27k standards naturally includes many aspects of IT but does not stop there. The introduction to ISO/IEC 27002 states explicitly:
”The value of information goes beyond written words, numbers and images: knowledge, concepts, ideas and brands are examples of intangible forms of information. In an interconnected world, information and other associated assets deserve or require protection against various risk sources, whether natural, accidental or deliberate.”
Generally speaking, an organisation’s most valuable information assets belong to business units, departments or functions other than IT Department. IT typically owns, manages and is accountable for protecting the shared IT infrastructure (i.e. the main corporate IT systems and networks delivering shared/cloud IT services to the business) which is a substantial information asset in its own right. However, in information security terms IT typically acts as a custodian (but not owner) for most business data on the systems and networks, including content belonging to other parts of the organisation or to suppliers, customers, business partners, sales prospects, stakeholders and other third parties.
This has important implications. Information/risk owners are accountable for ensuring that their information assets are adequately protected, just like other corporate assets. While information asset owners generally delegate key responsibilities for information security to Information Security and/or IT, they remain accountable and must ensure that information security is adequately funded, directed and supported to achieve the necessary level of protection. Likewise, Information Security and IT generally act as advisors and custodians with a duty to protect the information/data placed in their care, but they are not ultimately accountable for most information security incidents, breaches and impacts that occur as a result of unwise risk management decisions (such as under-funding security or accepting risks) made by the actual information asset owners.
Implementation tip: when assessing and treating information risks, focus primarily on critical business processes and valuable business information rather than the associated IT systems and data. The modern approach to corporate governance means that naive or duplicitous business managers can no longer blame and cower behind IT if they make inappropriate decisions or fail to act in order to identify and protect vital information assets. However, they often need help to appreciate and satisfy their security obligations.
Oh and by the way, “IT” is not the only important technology. What about Operational Technology, Network and comms Technology, Virtual Technology, Mobile Technology and Smart Technology? Take off those IT blinkers!
Top
FAQ: “Where can I obtain [insert name of any ISO27k standard here]?”
A: Published ISO27k standards may be purchased directly from the ISO store or from national standards bodies and commercial outlets such as Amazon (affiliate link).
It is worth checking for localized/national versions of the standards. Several national standards bodies release translated versions of the standards in their local languages. They go to great lengths to ensure that the translations remain true to the originals, although naturally this takes time.
ISO27k standards can generally be purchased as electronic documents or printed hardcopies. In addition to single-user PDFs, standards bodies may license electronic versions of the standards for multi-user internal corporate use - handy to make the definitive standards available on your intranet. User-based licenses are also required to incorporate the contents of standards into applications such as ISMS support systems. However, multi-user licenses are even more costly than the single-user licenses. [Don’t shoot the messenger! We don’t set the prices.]
Implementation tip: Google/shop around for the best deal. Before you crack-open your digital purse, check that you are in fact purchasing/licensing the correct edition, as old, deprecated standards remain on sale for some while after new editions have been released.
Top
FAQ: “I want to become an ISO27k consultant. I’m looking for books or courses that teach ISO27k. Is there an exam? ... ”
A: The best reference sources on the ISO27k standards are the standards themselves - in other words, you should buy and read the standards (see above). Being standards, they are quite formal in style but readable and useful. If you are going to implement them, write policies based upon them, consult around them etc. you will inevitably have to become very familiar with them so buy your copies and start reading!
The following ISO27k standards well worth studying:
- ISO/IEC 27000 introduces and gives an overview of the whole suite of ISO27k standards, and provides a glossary defining various information security terms specifically as they are used in the context of the standards.
- ISO/IEC 27001 formally specifies the system for managing information security. Along with ISO/IEC 27006, it is essential if you intend to become an ISMS certification auditor by taking a “ISO/IEC 27001 Lead Auditor” training course offered by various training, consultancy and certification companies, and completing the requisite number of compliance audits under the wing of a fully-qualified ISMS certification auditor. If you are looking to implement rather than certify compliance with the standard, you should also study ISO/IEC 27002 and others.
- ISO/IEC 27002 is a catalogue of generic information security controls. It is a practical standard offering oodles of advice for those choosing/designing and implementing information security controls. The best way to learn ISO/IEC 27002 inside-out is to use it for real, which means going all the way through one or more ISMS implementations from planning to operations, auditing and maintenance. If you have no prior experience in information security, you should try to find an experienced mentor or guide, or perhaps take a course for relevant qualifications (see next FAQ). Professional organisations such as ISSA, ISF and ISACA can help, along with the free ISO27k Forum.
- ISO/IEC 27003 explains the process for implementing ISO27k.
- ISO/IEC 27004 concerns metrics - an advanced topic that will become ever more important as your experience builds.
- ISO/IEC 27005 concerns the management (analysis, evaluation and treatment) of information risks and as such underpins all the ISO27k standards.
You should also be aware of the remaining ISO27k standards and have some familiarity with other similar/related standards, methods, laws etc. (such as PCI-DSS, COBIT and GCPR).
As to becoming a consultant, you are well advised to start by building a solid technical understanding of governance, risk and control concepts, and establishing your own expertise, experience, competence and hence credibility.
Implementation tip: by all means join the free ISO27k Forum. If you are struggling with particular ISMS-related issues, the archive of Forum messages well worth browsing or searching (it’s a Google group so the search function works pretty well ...), and members can always seek fresh answers to current issues and challenges. We’re here to help.
Top
FAQ: “Are there any qualifications for ISO27k professionals?”
A: Kind of. Other than the ISO and national standards bodies’ processes for checking and accrediting organisations who wish to offer ‘official’ compliance certification services, there is currently no equivalent of, say, ISACA or (ISC)2 overseeing the ISO27k courses and qualifications in order to set and maintain professional standards, insist on continuous professional development and so forth. At present there is nothing to stop anyone offering “ISO27k Lead Implementer” training courses and issuing certificates like confetti. This unfortunate situation casts doubt on the validity of Lead Implementer certificates in particular, and potentially discredits both the organisations currently offering them and the candidates who obtain them, even though they may be truly excellent. It’s a question of assurance not quality.
There are a number of ISMS-related training courses that hand out certificates of completion but I would not necessarily call them ‘qualifications’ on that basis alone. ‘Designations’ may be a better term.
The two most common types of ISMS-related designations are as follows.
ISO/IEC 27001 Lead Auditor (LA)
The term “Lead Auditor” was coined by training schemes that were initially designed and run internally by accredited ISO/IEC 27001 certification bodies in order to train up their own staff to perform certification audits. Subsequently, various public/commercial LA training courses have emerged. There are at least four possible routes to someone calling themselves an ISO/IEC 27001 LA:
- The highway: spend 5 straight days on a suitable officially-recognised training course run by an officially-recognised training body, pass the end of course exam, then undertake a further 35 days of third party certification audits under the guidance of a registered ISO/IEC 27001 LA. This route is preferred by the International Register of Certification Auditors and, in Japan, JRCA. The highway naturally suits students who are employed by the accredited certification bodies, since they can get both the classroom training and on-site experience from their employers.
- The country route: complete some other form of ISMS/audit related training (for example modular courses comprising a day or two’s training on ISMS plus 3 days on auditing), then undertake further ISMS assignments such as internal ISMS audits, ISMS-related consultancy gigs or third party certification audits, and finally pass some form of “on-site skills examination”. The country route may be the best option for students not working for accredited certification bodies, but may not deliver as much assurance.
- The cross-country 4x4 route: become a qualified and experienced information security professional and a qualified and experienced IT audit professional and gain lots of real-world experience of designing, building, implementing, managing, maintaining and advising on ISO27k ISMSs. Most professionals with more than, say, a decade or two’s work experience crossing these three areas have amassed valuable expertise, knowledge and battle scars, having faced many situations in the field. Some of them go on to take the highway or the country route, while others are too busy working for their clients or sharing their expertise with their employers to worry about certificates per se.
- The back alleys: a few students and consultants allegedly don’t bother with the hardship of actual training, exams and/or on-the-job experience, simply adding “ISO/IEC 27001 LA” (or similar) to their CVs and email signatures and carrying on regardless ...
By the way, that’s lead as in dog, not the dense grey metal.
ISO/IEC 27001 Lead Implementer (LI)
In response to market demand for help with implementing the ISO27k standards rather than just auditing ISMSs against ISO/IEC 27001, a number of IT training companies offer commercial ISO/IEC 27001 LI courses. These aim to give students some familiarity with the ISO27k standards, and then presumably provide pragmatic guidance on how to apply them to the design and implementation of an ISMS.
As with ISO/IECc 27001 LAs, do not rely on a candidate’s claimed LI qualification alone if information security is important to you - and why else would you be employing them? Skills (both technical and social), expertise, competencies and experience all vary from person to person, as does trustworthiness.
Caveat emptor! If you are employing information security professionals on the basis of their competence and integrity (trustworthiness), it pays to check carefully into their backgrounds. Verify their claims. See ISO/IEC 27002 for sage advice on this very point.
Note: ISO/IEC 27021 lays out the skills and competencies expected of professionals in this field. Training providers are hopefully aligning their course curricula with the standard, hence the course-completion certificates will have more meaning and value.
Implementation tip: in my considered opinion, demonstrable hands-on ISO27k standards implementation and audit experience, ideally with more than one organisation, is by far the best “qualification” in the field. Next best would be demonstrable consultancy experience, helping a number of clients design, install and run their ISMSs, preferably again with a considerable amount of hands-on work and not merely advising at a distance. The LA and particularly the LI certifications vary in credibility but nevertheless the courses are a valuable introduction for beginners, although students who already have a reasonable understanding of information security management concepts are more likely to benefit from ISO27k-specific training plus general information security and IT audit qualifications such as CISSP, CISM and CISA, and general business management qualifications such as MBAs.
Top
FAQ: “Where else can I find answers on ISO27k and information security?”
A: Besides this FAQ and the ISO27k standards themselves, there are several professional/special interest groups and forums (fora?) worth considering:
- ACM SIGSAC (Association for Computing Machinery - Special Interest Group - Security, Audit and Control). Mission: “to develop the information security profession by sponsoring high-quality research conferences and workshops.”
- CSA (Cloud Security Alliance) is “the world’s leading organisation dedicated to defining and raising awareness of best practices to help ensure a secure cloud computing environment. CSA harnesses the subject matter expertise of industry practitioners, associations, governments, and its corporate and individual members to offer cloud security-specific research, education, certification, events and products. CSA’s activities, knowledge and extensive network benefit the entire community impacted by cloud - from providers and customers, to governments, entrepreneurs and the assurance industry - and provide a forum through which diverse parties can work together to create and maintain a trusted cloud ecosystem.”
- InfraGard: “InfraGard is a partnership between the FBI and members of the private sector. The InfraGard program provides a vehicle for seamless public-private collaboration with government that expedites the timely exchange of information and promotes mutual learning opportunities relevant to the protection of Critical Infrastructure. With thousands of vetted members nationally, InfraGard's membership includes business executives, entrepreneurs, military and government officials, computer professionals, academia and state and local law enforcement; each dedicated to contributing industry specific insight and advancing national security.”
- ISACA (originally the Information Systems Audit and Control Association). “As a nonprofit, global membership association for IT and information systems professionals, ISACA is committed to providing its diverse constituency of more than 140,000 professionals worldwide with the tools they need to achieve individual and organisational success. The benefits offered through our globally accepted research, certifications and community collaboration result in greater trust in, and value from, information systems. Through more than 200 chapters established in more than 80 countries, ISACA provides its members with education, resource sharing, advocacy, professional networking, and a host of other benefits on a local level.”
- (ISC)² (International Information Systems Security Certification Consortium) is “an international, nonprofit membership association for information security leaders like you. We’re committed to helping our members learn, grow and thrive. More than 140,000 certified members strong, we empower professionals who touch every aspect of information security.”
- ISO27k Forum (ISO/IEC 27000-series standards discussion forum). “Since its launch back in 2006, the ISO27k Forum has grown steadily into a supportive and friendly global community of~4,500 information security professionals, most of whom are actively using the ISO/IEC 27000-series standards and are willing to share their queries, experience and expertise freely with others. This is a practitioner’s group with a practical focus, where (almost!) every contribution is treasured and every member valued. We mostly discuss matters of interest and concern to those interpreting and applying the ISO27k standards in real world situations.” Best of all, it’s entirely free of charge, and remarkably free of spam.
- ISSA (Information Systems Security Association) is “a nonprofit organisation for the information security profession committed to promoting effective cyber security on a global basis: Being a respected forum for networking and collaboration; Providing education and knowledge sharing at all career lifecycle stages; Being a highly regarded voice of information security that influences public opinion, government legislation, education and technology with objective expertise that supports sound decision-making.”
- OWASP (Open Web Application Security Project) is a “worldwide not-for-profit charitable organisation focused on improving the security of software. Our mission is to make software security visible so that individuals and organisations are able to make informed decisions. OWASP is in a unique position to provide impartial, practical information about AppSec to individuals, corporations, universities, government agencies, and other organisations worldwide. Operating as a community of like-minded professionals, OWASP issues software tools and knowledge-based documentation on application security.”
Implementation tip: questions are good. I learn a lot from questions to the ISO27k Forum. I also learn a lot by answering questions and considering other people’s answers, further responses, corrections, clarifications, retrenchments and counterpoints. Despite the popular mantra, there are dumb questions ... but there are also deceptively simple questions that turn out to be extremely insightful and deep once we peel back the layers to respond. Whatever your initial state of knowledge, expertise and experience, actively engaging in the debate puts you on the fast track to further personal and professional development. Do join in. Remember: life is not a spectator sport.
Top
FAQ: “What does ‘ISO’ mean? And what about ‘ISO/IEC’?”
A: ISO is the short or common name of the global standards body known in English as the International organisation for Standardization. “ISO” is not strictly an abbreviation since the long name varies in different languages - it is in fact derived from the Greek word isos meaning equal. At least, that’s what we’re told.
IEC is the International Electrotechnical Commission, another international standards body that cooperates closely with ISO on electrical, electronic and related technical standards. Standards developed jointly with ISO are prefixed “ISO/IEC”.
ISO/IEC also collaborate on some standards with other international organisations (both governmental and private sector) such as the International Telecommunication Union, a trade body coordinating telecomms organisations and practices to enable worldwide communications.
Implementation tip: we have tried to use “ISO/IEC” consistently throughout this site when referring to applicable standards, but we know it’s a mouthful. In casual conversation, management reports, security awareness materials, social media etc. “ISO” is good enough for most purposes. Don’t sweat the small stuff.
Top
FAQ: “What is the meaning of ‘WD’, ‘CD’, ‘FDIS’ and other abbreviations scattered-about like confetti at a massive wedding in ISO-land?”
A: ISO/IEC JTC 1 Standing Document N 18 lists these abbrev’s, most of which are rarely seen:
- AG - Advisory Group
- AMD - Amendment
- ARO - Approved RS Originator
- BRM - Ballot Resolution Meeting
- CB - [IEC] Council Board
- CD - Committee Draft
- CDV - [IEC] Committee Draft for Vote
- COR - Technical Corrigendum
- CS - [ISO] Central Secretariat
- DAM - Draft Amendment
- DCOR - Draft Technical Corrigendum
- DIS - [ISO] Draft International Standard
- DoC - Disposition of Comments
- DR - Defect Report
- DTR - Draft Technical Report
- DTS - Draft Technical Specification
- FDAM - Final Draft Amendment
- FDIS - Final Draft International Standard
- HoD - Head of Delegation
- ICT - Information and Communications Technology
- IEC - International Electrotechnical Commission
- IPR - Intellectual Property Rights
- IS - International Standard
- ISO - International Organization for Standardization [a name, not an abbreviation]
- ITTF - Information Technology Task Force
- ITU - International Telecommunication Union
- ITU-R - International Telecommunication Union - Radiocommunications Sector
- ITU-T - International Telecommunication Union - Telecommunication Standardization Sector
- JCG - Joint Coordination Group [as opposed to the disjointed ones?]
- JTAB - Joint Technical Advisory Board
- JTC 1 - ISO+IEC Joint Technical Committee number 1
- JWG - Joint Working Group
- MB - (ISO) Member Body
- NB - National Body e.g. British Standards, Standards New Zealand.
- NC - (IEC) National Committee
- NP - New work item Proposal
- NWI - New Work Item
- OWG - Other Working Group [they were running out of ideas for naming]
- PAS - Publicly Available Specification
- PC - Project Committee
- PDAM - Proposed Draft Amendment
- PDTR - Proposed Draft Technical Report
- PDTS - Proposed Draft Technical Specification
- PT - Project Team
- PWI - Preliminary Work Item
- RER - Referencing Explanatory Report
- RG - Rapporteur Group
- RS - Referenced Specification
- SC - SubCommittee
- SD - Standing Document
- SG - Study Group
- SMB - (IEC) Standardization Management Board
- SWG - Special Working Group [as opposed to those ordinary ones]
- TAG - (ISO) Technical Advisory Group
- TC - Technical Committee
- TMB - Technical Management Board
- TR - Technical Report
- TS - Technical Specification
- WD - Working Draft
- WG - Working Group
The standards production process from start (PWI) to publication (IS) normally takes between 2 and 4 years with a mean of 2.8 years, given the attention to detail at every stage and the need for collaboration and consensus on a global scale e.g. when a WD is issued for comments, representatives of the national standards bodies that belong to ISO or IEC (known as Member Bodies within ISO or National Committees in IEC) typically have 2 or 3 months to review the document, discuss it amongst themselves and submit formal votes and comments. If the comments are unfavourable or complex, an updated WD is normally released for a further round of comments. When documents have stabilised, they are circulated for voting. Any of you with experience of getting formal documents such as security policies prepared, reviewed and approved by your management will surely appreciate the ‘fun’ involved in doing this in an international arena!
A fast-track process is sometimes used to adopt an existing national standard as an ISO standard. Some 6 months is allowed for comments and no more than a quarter of the votes may be negative if the standard is to be approved. “Fast” is of course a relative term. We’re talking months or years here, not femtoseconds.
Published standards are supposed to be reviewed every five years, or earlier if defect reports are formally submitted. They are not necessarily updated, however: they may be withdrawn if no longer relevant, or confirmed as-is if changes are not needed.
Top
FAQ: “Aside from International Standards, what are TRs and PASs and ... ?”
A: ISO/IEC publishes various types of standards on a wide range of subjects:
- An International Standard (IS) is the most common form of ISO/IEC standard, including product/technical standards, test methods, ‘codes of practice’ (good practices) and management standards. An IS “provides rules, guidelines or characteristics for activities or for their results, aimed at the achievement of the optimum degree of order in a given context”. Most aim to describe the final objective without prescribing the method of getting there (although they don’t all meet that aim!). The review cycle is 5 years (maximum).
- A Technical Specification (TS) is a standard on a immature subject that is still being developed, and is not quite ready to become a full IS. Feedback is encouraged in order to drive further development and lead, eventually, to the release of an IS. Internally within the committee, final drafts are called PDTS Proposed Draft Technical Specifications.
- A Technical Report (TR) is a guideline rather than a specification. It may draw on surveys and ‘informative reports’, and may attempt to describe the ‘state of the art’. Internally within the committee, final drafts are called PDTR Proposed Draft Technical Reports.
- A Publicly Available Specification (PAS) responds to an urgent need to drive consensus on some emerging topic. Alternative and perhaps incompatible views may be expressed by parallel PASs from different expert streams. A PAS is supposed to be replaced by a TS or IS, or withdrawn, within 6 years.
- An International Workshop Agreement (IWA) is essentially an alien PAS produced outside of the ISO/IEC world - for example by some technical or industry body. It too has a maximum life of 6 years.
Top
FAQ: “What is meant by ‘JTC 1/SC 27’ and what are ‘WG’s’?”
A: As you might expect, an international body developing and coordinating a vast range of technical standards on a global basis has evolved a correspondingly vast bureaucracy to manage and share the work. Member Bodies (that is, members of ISO, in other words national standards bodies and industry groups) are classified as
- P-members - actively Participating in the standards development and maintenance work, with obligations to provide inputs from their experts and vote in the formal stages leading up to the publication of standards;
- O-members - officially just Observing proceedings, in practice engaging and contributing occasionally without committing to do so, and without voting rights;
- L-members - these are other ISO/IEC committees and industry/trade bodies who Liaise or collaborate with the standards committees, providing specialist inputs and guidance on points of common interest. Coordinating and aligning standards across the entire portfolio of topics is an important and complex task.
Members normally participate in the development of standards through Technical Committees established by the respective organisations to deal with particular fields of technical activity. IT standardisation presents unique requirements and challenges given the pace of innovation. Therefore, in 1987, ISO and IEC established a Joint Technical Committee ISO/IEC JTC 1 to share responsibility for IT standards, taking over from the earlier TC 97.
JTC 1’s purpose is “Standardization in the field of Information Technology” which “includes the specification, design and development of systems and tools dealing with the capture, representation, processing, security, transfer, interchange, presentation, management, organisation, storage and retrieval of information.” While there is general agreement that information security is a superset of IT security, the unfortunate fact that the ISO/IEC committee has “Information Technology” in its official title means that the ISO27k information security standards are often mistaken for IT standards.
In ISO-speak, “SC” is a Sub-Committee. SC 27 was formed in April 1990. SC 27 is just one of several Sub-Committees of ISO/IEC JTC 1 responsible for information security-related standards. Others include:
- SC 6 - Telecommunications and information exchange between systems
- SC 7 - Software and systems engineering
- SC 17 - Cards and personal identification
- SC 25 - Interconnection of information technology equipment
- SC 29 - Coding of audio, picture, multimedia and hypermedia information
- SC 31 - Automatic identification and data capture techniques
- SC 32 - Data management and interchange
- SC 36 - Information technology for learning, education and training
- SC 37 - Biometrics
SC 27’s Standing Document 1 lays out its key processes in 50 pages of excruciating detail. As you may have guessed, there are a few more SDs. Essentially these constitute the committee’s internal policies, operating procedures and guidelines.
SC 27 owns and maintains more than 200 standards of which around a quarter are actively progressing at any one time. SC 27, in turn, has carved-up its workload across five Working Groups:
- SC 27/WG 1 - Information Security Management Systems: responsible for developing and maintaining ISMS standards and guidelines, identifying requirements for future ISMS standards and guidelines, maintaining the WG1 roadmap and liaising/collaborating with other organisations and committees in relation to ISMS;
- SC 27/WG 2 - Cryptography and Security Mechanisms: cryptography, cryptographic algorithms, encryption, authentication, key management, digital signatures and all that;
- SC 27/WG 3 - Security Evaluation, Testing and Specification: Common Criteria, evaluation methods, protection profiles, security capability maturity models etc.;
- SC 27/WG 4 - Security Controls and Services: responsible for a variety of standards covering intrusion detection, IT network security, incident management, ICT disaster recovery, use of trusted third parties, business continuity, application security, cybersecurity and outsourcing. Some of these have ISO27k numbers but may not be considered part of “the ISO/IEC 27000 family of standards” as it is officially known;
- SC 27/WG 5 - Identity Management and Privacy Technologies: does pretty much exactly ‘what it says on the tin’ (the title is self-explanatory). Includes biometrics.
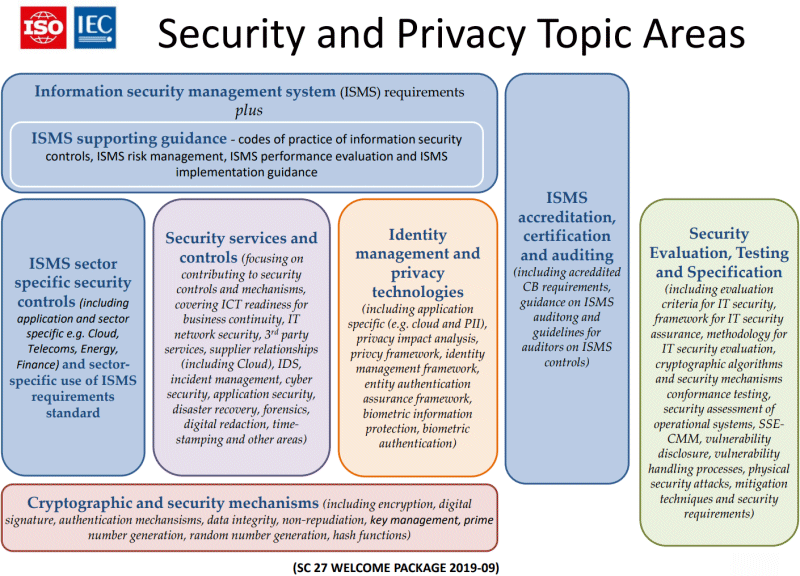
As if that wasn’t complicated enough, there are also several Advisory Groups (covering concepts such as management, trustworthiness, terms and strategy for SC 27) and, from time to time, Other Working Groups, Special Working Groups, Rapporteur Groups (advisors), Ad Hoc Groups, Joint Working Groups, Workshops and the IT Task Force - a veritable abbreviation stew.
Implementation tip: once you have gained ISMS implementation experience, consider helping the continued development of the ISO27k standards by contacting your national standards body and volunteering your assistance (more advice follows ...).
Please note: this website - ISO27001security dotcom - is privately owned and is NOT an official organ of ISO/IEC. Please read our disclaimer for more.
Top
FAQ: “How can I keep up with developments in ISO27k?”
A: An easy way to keep in touch with developments is to bookmark this website. Call back from time to time to check the news/updates section on the home page, and hunt for the  blobs. blobs.
Another option is to Google ISO/IEC 27000 or related terms. Professional information security-related organisations such as ISSA and ISACA are increasingly discussing or publishing articles on ISO27k. There are a few ISO27k groups on Linkedin and other social media, of variable quality and focus: unlike our ISO27k Forum, most are plagued by spam.
Implementation tip: if you discover some ISO27k news before it is published here, please tell us so we can share it with the user community via this website and/or via the ISO27k Forum.
Top
FAQ: “How can I get involved in the development of security standards?”
A: Contact your national standards body (e.g. BSI, NIST, ANSI, SNZ) to find out about any special interest groups and committees working in the information security arena. If you can spare the time to get involved with standards specification, development and/or review, contact your local ISO/IEC JTC 1/SC 27 representative/s to volunteer your services.
There is a genuine opportunity for experienced professionals to influence the future directions of ISO27k if they are prepared to put in the time and effort to collaborate with colleagues around the world. Don’t wait until the standard is published to express criticisms or suggest improvements: get involved in the drafting and review process!
Implementation tip: the ISO/IEC security Sub-Committees and Working Groups are extremely busy and produce lots of paperwork. Committee work drafting and reviewing standards plus responding to queries from other interested parties has to be slotted-in with other duties including the day-job. If you get involved, be prepared to lose a substantial chunk of your free time reading, reviewing and contributing to draft standards. It’s fun though, a privilege to be able to collaborate with professional peers committed to ISO27k.
Top
FAQ index Next FAQ section >
|