|
< Previous standard ^ Up a level ^ Next standard >
ISO/IEC TS 27110:2021  — Information security, cybersecurity and privacy protection — Cybersecurity framework development guidelines (first edition) — Information security, cybersecurity and privacy protection — Cybersecurity framework development guidelines (first edition)
Abstract
“[ISO/IEC TS 27110] specifies guidelines for developing a cybersecurity framework. It is applicable to cybersecurity framework creators regardless of their organisations' type, size or nature.” [Source: ISO/IEC TS 27110:2021)]
Introduction
This Technical Specification offers guidance for those within organisations who are creating cybersecurity frameworks, defined as “basic sets of concepts used to organize and communicate cybersecurity activities”.
Scope of the standard
The standard “specifies guidelines for developing a cybersecurity framework.”
Content of the standard
The main sections are:
5 Overview
6 Concepts
6.1 General
6.2 Identify
6.3 Protect
6.4 Detect
6.5 Respond
6.6 Recover
7 Developing a cybersecurity framework
Annex A: outlines some inputs, activities and outputs for each of the identify, protect, detect, respond and recover stages.
Annex B: “Considerations in the integration of a cybersecurity framework”, purpose unclear.
Annex C: a listing of (mostly) national cybersecurity frameworks.
Status
The first edition was published as a Technical Specification in 2021 and confirmed unchanged in 2024.
Personal comments
The intended audience and purpose of this standard is hard to fathom. Who is it for, and what is a “cybersecurity framework” anyway? Whose ‘burden’ is it seeking to lighten, and what is the nature of their burden?
- According to the introduction, “business groups, government agencies, and other organisations produce documents and tools called cybersecurity frameworks to help organize and communicate cybersecurity activities of organisations”. My toolbox contains no “cybersecurity frameworks” so I guess this standard is not aimed at me;
- The standard makes no attempt to explain what it means by ‘cybersecurity’. This is yet another ISO27k ‘cybersecurity’ project that studiously avoids defining the term, using woolly language to confuse instead of clarify. So much for international standards pushing back the frontiers;
- The distinction between “creators” and “implementors” of “cybersecurity frameworks” implies a conventional waterfall approach i.e. someone first identifies requirements, designs and develops a solution (the “framework”) which someone else then puts into operation. There is no hint presently that the process might be iterative, or that both phases would need to be governed and managed appropriately. However, I’m guessing here since the standard does not elaborate: it simply states that framework creators are its intended audience;
- The ‘concepts’ that (according to the standard) “should be included in a cybersecurity framework” simply reflect the usual pre-, para- and post-incident stages, another simplistic linear timeline. This is hardly rocket surgery. However, the standard makes no attempt to justify why these specific ‘concepts’ ‘should’ be ‘included’, and completely ignores the possibility of other potential ‘concepts’ or framework structures (such as <ahem> ISO/IEC 27001 to name but one of several);
- The examples listed in Annex C suggest a “cybersecurity framework” might be a strategic approach for dealing with (presumably IT and Internet-related information) risks to critical national infrastructures, implying therefore that the ‘cybersecurity framework creators’ would be government officials. But I’m guessing again, pecking between the lines like a hungry chicken for tiny crumbs of sense.
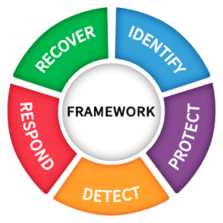 The relationship between a “cybersecurity framework” and a conventional ISMS remains unclear at this point. Those “documents and tools” sound to me suspiciously like the embodiment of a management system, despite the draft standard stating categorically “This document is not intended to supersede or replace the requirements of an ISMS given in 27001” [sic]. The relationship between a “cybersecurity framework” and a conventional ISMS remains unclear at this point. Those “documents and tools” sound to me suspiciously like the embodiment of a management system, despite the draft standard stating categorically “This document is not intended to supersede or replace the requirements of an ISMS given in 27001” [sic].
To my cynical eye, this looks suspiciously like an attempt to align ISO27k with - or perhaps amend ISO27k to embody - NIST’s CyberSecurity Framework specifically. Organisations that prefer the CSF are of course free to adopt it, so why change ISO27k, especially while “cybersecurity” remains a solid-gold buzzword that consistently defies definition? Oh I despair!
< Previous standard ^ Up a level ^ Next standard >
|